Pallet Security & Technical Overview


System Architecture
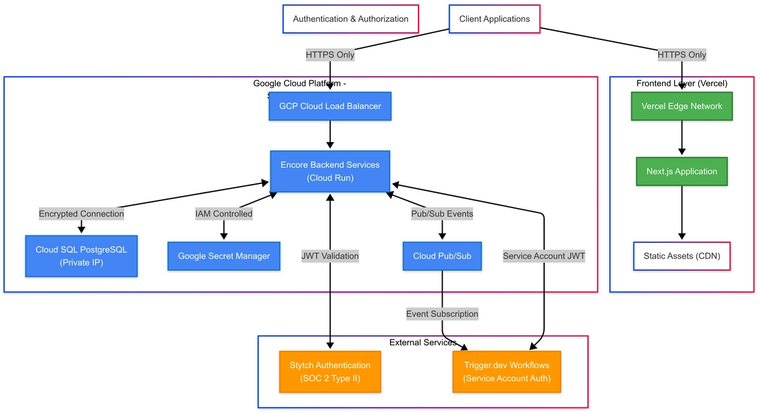
Pallet operates on Google Cloud Platform with a cloud-native architecture employing defense-in-depth security controls:
Certifications
Pallet is SOC 2 Type II certified; GDPR compliant; operating under CCPA regulations.
Authentication & Authorization
User Authentication
- Primary Authentication: Stytch passwordless authentication platform (SOC 2 Type II certified)
- Multi-Tenancy: Organization-scoped access with role-based permissions (Admin, Member, External)
- Session Management: JWT-based sessions with configurable expiration
Service Account Authentication
Internal services authenticate using RS256-signed JWTs with the following controls:
- Audience validation preventing token reuse across services
- Email allowlisting for approved service accounts only
- Short-lived tokens with automatic expiration
Google Cloud Platform Infrastructure
Cloud Run Security
- Container isolation using Cloud Run's sandbox environment
- Automatic security updates and vulnerability scanning
- No persistent local storage - all data encrypted at rest in Cloud SQL
Network Security
- HTTPS/TLS 1.3 enforcement for all external communication
- Cloud Load Balancer with DDoS protection and traffic filtering
- Private IP addressing for database connections
- VPC network isolation for internal service communication
Identity and Access Management (IAM)
- Principle of least privilege for all service accounts
- Fine-grained permissions for GCP resource access
- Automated permission management and access reviews
Database Security
Cloud SQL PostgreSQL
- Encryption: AES-256 at rest, TLS in transit
- Network Isolation: Private IP access within VPC only
- Access Control: Credentials managed via Google Secret Manager
- Backup Security: Automated encrypted backups with point-in-time recovery
- Audit Logging: Comprehensive database access logging
Multi-Tenant Data Isolation
-- Organization-scoped data access enforcement
CREATE POLICY organization_isolation ON secrets
FOR ALL TO application_role
USING (organization_id = current_setting('app.current_organization_id'));Secrets Management
Google Cloud Secret Manager
- Centralized storage for all sensitive data (API keys, tokens, credentials)
- Automatic secret rotation with versioning
- Environment-specific secret management (dev/staging/production)
- IAM-controlled access to secrets
Development Environment
- Local encrypted storage for development secrets
- Git-ignored local files preventing accidental commits
- Same API interface across all environments
Data Protection
Encryption Standards
- Transit: TLS 1.3 for all external connections, encrypted GCP internal communication
- Rest: Database encryption using Google-managed keys, Secret Manager envelope encryption
- Logs: Encrypted application logs with compliant retention policies
Security Monitoring
Logging and Audit
- Structured logging for authentication attempts and API access
- Real-time security event monitoring and alerting
- Audit trails for all data access and modifications
- Google Cloud Security Command Center integration
Threat Detection
- Automated container vulnerability scanning
- Network traffic analysis for anomaly detection
- Regular security assessments and penetration testing
Summary
Pallet implements enterprise-grade security through Google Cloud Platform's infrastructure, dual authentication systems (Stytch for users, service account JWTs for services), comprehensive encryption standards, and multi-tenant data isolation. The architecture provides defense-in-depth protection while maintaining scalability for AI-powered logistics workflow automation.
CoPallet Large Language Model (LLM) Architecture & Security
Multi-Model Routing Framework
CoPallet employs an open-source framework for intelligent LLM request routing with automatic failover capabilities. This architecture ensures high availability and optimal performance across diverse AI models.
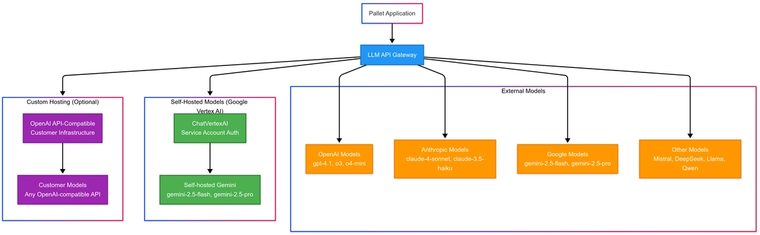
Supported Model Providers
External Models
- OpenAI: GPT-5, GPT-5-mini, o3
- Anthropic: Claude-4-Sonnet
- X.ai: Grok-4, Grok-3-mini
Self-Hosted Models (Google Vertex AI)
- Direct integration with Google Cloud Vertex AI
- Service account authentication with cloud-platform scopes
- Models available:
- Google: Gemini-2.5-Flash, Gemini-2.5-Pro
- DeepSeek: R1 models
- Meta: Llama-4-Scout, Llama-4-Maverick
- Qwen: 32B variants
-
Custom Hosting Support
- Compatible with any OpenAI API-compliant endpoint
- Supports customer-managed model deployments
- Flexible authentication and routing configuration
- Allows organizations to use their own model infrastructure
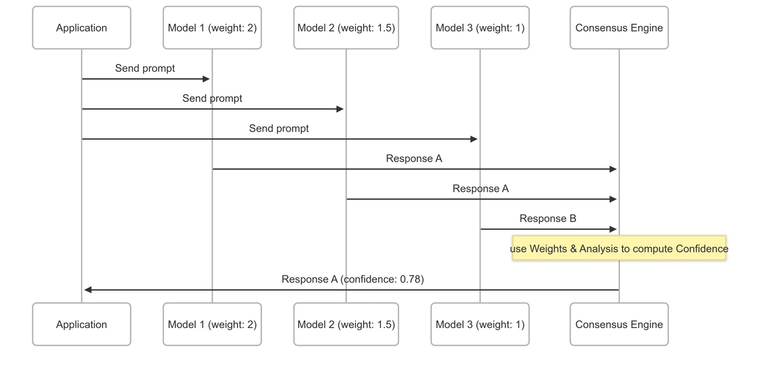
Consensus-Based Response Generation
CoPallet implements a sophisticated consensus mechanism to ensure accuracy and reliability of AI responses through multi-model validation.
Confidence Scoring & Model Weights
Different models are assigned weights based on their performance characteristics and reliability for specific tasks. We employ an LLM-Based Analysis Method. This approach uses a dedicated model to analyze response variations from multiple AI models, considering both the assigned model weights and the overall quality of responses to provide detailed reasoning for confidence assignments. The analysis model evaluates agreement patterns, response consistency, and data quality to generate nuanced confidence scores that reflect the reliability of the consensus decision.
Consensus Process Flow
Security Controls for LLM Operations
API Key Management
- All external model API keys stored in Google Secret Manager
- Environment-specific key rotation and access control
- Encrypted transmission of all API requests
- No API keys stored in application code or configuration files
Self-Hosted Model Security
- Service account authentication for Vertex AI access
- VPC-isolated model endpoints within Google Cloud
- Audit logging for all model inference requests
- IAM-controlled access to AI project resources
Request Validation & Security
- Input sanitization and prompt injection prevention
- Structured output validation using JSON schemas
- Cost prediction and usage monitoring for budget control
- Rate limiting to prevent abuse and manage costs
Data Privacy & Compliance
- No persistent storage of prompts or responses in external services
- Model responses processed in-memory with secure cleanup
- Organization-scoped data isolation maintained across all LLM operations
- Compliance with data residency requirements through model selection
Automatic Failover & Reliability
Unified LLM API Gateway Benefits
- Universal Failover: Automatic routing to available models when primary models are down, regardless of hosting location
- Centralized Load Balancing: Intelligent distribution across all configured models (external, self-hosted, and customer-hosted)
- Real-time Status Monitoring: Unified monitoring of model availability across all providers
- Transparent Operations: Failover occurs without application code changes, maintaining consistent API interface
Enhanced Redundancy Strategy
- Multiple models across different hosting environments capable of handling the same task types
- Graceful degradation when high-weight models are unavailable (whether external, self-hosted, or customer-hosted)
- Cross-provider backup capabilities for maximum reliability
- Health checks and automatic retry mechanisms managed centrally by OpenRouter
Integration Patterns
Structured Output Generation
const response = await llmService.generateWithStructuredOutput({
prompt: "Extract invoice data from this document",
schema: invoiceSchema,
schemaName: "invoice_extraction"
model: "gpt-5"
});Multi-Model Consensus
const consensusModels = [
{ model: 'gpt-5' },
{ model: 'o3' },
{ model: 'gemini-2.5-pro' },
{ model: 'grok-4' },
{ model: 'llama-4-maverick' },
{ model: 'gemini-2.5-pro' }
];
const result = await digitizer.digitize({
content: document,
schema: extractionSchema,
confidenceMethod: 'llm-judge' | 'pure-confidence'
});Conclusion
CoPallet's security architecture provides enterprise-grade protection through defense-in-depth strategies, leveraging Google Cloud Platform's security capabilities, and implementing industry best practices for authentication, authorization, and data protection. Our commitment to security enables logistics companies to confidently adopt AI-powered workflow automation while maintaining the highest standards of data protection and regulatory compliance.
For additional security documentation or to discuss specific compliance requirements, please contact our security team.

